| YubiKey 5 NFC | Product: Yubikey 5 NFC for Mac |
| Website: https://www.yubico.com | Buy: Version 5NFC |
ABOUT YUBIKEY
Yubico was founded in Sweden 2007 with the mission to make secure login easy and available for everyone. In 2011, Stina, CEO & Founder, and Jakob, CTO, moved to Silicon Valley to make the dream happen. In close collaboration with the leading internet companies and thought leaders we created native support for our security keys in the major online platforms and browsers, enabling a safer internet for billions of people. They now offer a full range of YubiKey 2FA keys.
2FA BECOMES A NEEDED SECURITY TOOL
The internet was designed for sharing information, not security. As it has advanced and scaled to be a critical part of our everyday lives—so have the fraudsters. Today, 3.8 billion email accounts, login credentials are being compromised every day. Because of this huge number of global users, data has become more than just numbers and statistics. All data on the internet is in a way a valuable set of information about economic projects, security and private data such as, names, date of birth, social security numbers and your ( faulty assumption ) personal email. Your assumption that your email is a private matter is true, but millions of people are faced with hacked data and subsequently loose their anonymity on the internet and face massive problems. Problems that could lead to personality theft and huge financial problems, as most people don’t use password managers and/or safe places for their precious data.
On top of all this, most people use only ‘one password’ to cover all their logins from email to government or business related access. Security is underestimated by millions, which makes the internet a great place for fraud and hackings. I guess almost everybody’s email address has been compromised in some way ( mine does as well ), as we all have a gmail account, or subscriptions of a newspaper or others. You may sometimes even receive an email from your host warning you about a hack that has taken place and your data, credit card is stolen. Welcome to the club !
Besides using a password manager a 2 Factor Authentication is absolutely needed to keep yourself protected as much as possible. So my first suggestion to everybody is to get yourself Dashlane Premium to store your passwords etc. However just running Dashlane is not enough really as you want to keep any kind of access to just yourselves. This is why YubiKey was invented and now used by companies and private users all over the world.
YUBIKEY FEATURES
WHY IS YOUR DATA VALUABLE
1. Hackers can sell your data to other criminals
- One way hackers profit from stolen data is selling it in masses to other criminals on the dark web.
2. Stolen personal information is fuel for identity theft
- Identity theft is a crime in which the victim’s personal information is used to gain benefits at the victim’s expense. Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft.
3. Login details are needed for account takeover
- Criminals use stolen login credentials to break into accounts with payment details, such as shopping accounts. This is called account takeover, and it often leads to identity theft. If the hacker changes your password, you will also lose access to your account. Account takeover can be costly if the hijacked account includes payment details.
4. Stolen data is used to target phishing attacks and extortion
- With stolen personal information criminals can target victims with phishing attacks. In phishing scams victims are lured into giving information like credit card details willingly to criminals by masking the scam as something legit.
5. Stolen personal information can be used to harm companies
- In addition to the personal problems stolen data can cause, it can also damage companies. With stolen data criminals can target company personnel to give sensitive information or to trick them to make payments. Such phishing attacks targeted against a specific individual are called spear-phishing. Criminals can also try to gain access to company networks to spy on them and infect them with malware.
DATA HACKING IMPACT 2020
To give you an impression, about the impact of Data Hacking by criminals just read the statement below:
- Cybercrime will cost the world $6 trillion by 2021.
- By 2021, a business will fall victim to ransomware every 11 seconds.
- The cost of a data breach will reach $150 million by 2020.
- In 2023 alone, cybercriminals will steal 33 billion records.
- Americans lose $15 billion annually due to identity theft.
- 1 in 36 mobile phones had high-risk apps in 2018.
- It takes 196 days on average to identify a data breach.
HACKING STATISTICS 2020
Let’s check the latest statistics and see the numbers involved.
1. Hacking accounts for over half of all recent data breaches. In a 2020 report that analyzed nearly 4,000 confirmed breaches, it was found that:
- over half of them (52%) were a result of hacking
- hacking statistics gathered in the report show that the second biggest risk was phishing, which accounted for nearly 33% of all data breaches
- Malware is also a major culprit, responsible for 28% of the data breaches
The report also found that 70% of the breaches were financially motivated and, rather worryingly, 43% of the breaches involved exploiting vulnerabilities in web applications. This is more than double the numbers from 2019.
2. There is an average of 38.4 passwords in use for every human worldwide. (Source: SC Magazine)
- It is estimated that there are more than 300 billion passwords in use today or nearly an average of 38.4 passwords per individual. Among the Fortune 500 companies, the average employee is expected to manage double the world’s average at 90 business and personal accounts – that’s certainly a lot of passwords to remember!
3. In the last three years, the number of phishing websites has increased by over 130.5%. (Source: Google Transparency Report)
- Since 2017, the cyberworld has witnessed a worryingly rapid rise in phishing websites. As per cybercrime statistics from Google, the number of phishing websites grew from approximately 584,000 in that year to more than 1.35 million this year, representing an increase of over 130.5%.
- At the same time, the number of malware sites has taken a nosedive. In 2017, the estimated figure was 516,000. Today, the number is less than 53,300 websites.
4. 99.9% of accounts get hacked because of this one single reason. (Source: Windows Central)
- In January of this year, roughly 1.2 million Microsoft accounts were compromised. According to the company, 99.9% of them had one big thing in common when it came to vulnerability – they all did not make use of multi-factor authentication.
According to hacking statistics, the most commonly used method for hacking accounts is password spraying. This involves taking easy-to-guess passwords and going through a list of usernames until the right combination gives access to an account.
HOW DOES TWO FACTOR AUTHENTICATION WORK
YubiKey 5 NFC, stops account takeovers, and offers password-less and modern multifactor authentication. You should get the world’s leading security key for superior security, user experience and return on investment. YubiKey’s, primary role is as a second factor of authentication. In practice, Two-Factor Authentication (2FA) needs you to do a second thing after entering your password to prove it’s you / ownership. Authentication factors, listed in approximate order of adoption for computing, include the following:
- A knowledge factor is something the user knows, such as a password, a PIN (personal identification number) or some other type of shared secret.
- A possession factor is something the user has, such as an ID card, a security token, a cellphone, a mobile device or a smartphone app, to approve authentication requests.
- An inherence factor, more commonly called a biometric factor, is something inherent in the user’s physical self. These may be personal attributes mapped from physical characteristics, such as fingerprints authenticated through a fingerprint reader. Other commonly used inherence factors include facial and voice recognition. They also include behavioral biometrics, such as keystroke dynamics, gait or speech patterns.
(source: https://searchsecurity.techtarget.com/definition/two-factor-authentication)
ALTERNATIVES
Though this review primarily focuses at hardware 2FA, there also are many other ways/tools to add a second factor validation. Many sites will send you codes via SMS to verify your identity. Apps such as Duo (Free at Apple.com) and Authy rely on push notifications which are (in theory) harder to intercept than SMS messages. I also use DUO as a 2FA solution for some accounts, as you will need to ability from the host to actually add and integrate your YubiKey ( or other) in their system. This however is not yet adapted by all internet parties, which leaves you to stick to a 2FA software tool. Again, use this if possible, as it still makes things much more difficult for an hacker or data breach.
Whether you go with a hardware or software solution or a mix of both, do add 2FA wherever and whenever you can. When Google deployed 2FA keys internally, it saw successful account takeovers drop to zero. This proofs the significant contribution of Yubikey ( or Google’s Titan ).
YUBIKEY IN ANY FORMAT
Yubico has always offered several sizes and variations of its security keys to fit just about every need. This is great, because consumers and IT professionals can get exactly what they need at a variety of prices. The downside is that browsing the Yubico store is a frequently overwhelming experience. I’ll do my best to boil down the basics. To check which key would benefit your personal need just follow this link: https://www.yubico.com/nl/quiz/
There are four flavors of YubiKey 5 Series devices, including the $45 YubiKey 5 NFC reviewed here, as well as three other form factors: the $50 YubiKey 5 Nano, the $50 YubiKey 5C, and the $60 YubiKey 5C Nano. The ‘5 NFC’ is the only YubiKey to offer wireless communication, but besides that the only difference among these devices is size, price, and USB connector.

The two Nano devices are the least intrusive devices in the group and nestle within your USB-A or USB-C slots, easily within reach if you need them often. The YubiKey 5C uses a USB-C connector, is slightly smaller than the 5 NFC, and can hang on your keychain alongside the 5 NFC; it lacks wireless communication. You can, however, connect either the YubiKey 5C or 5C Nano directly to your Android device. The ‘nano-c’ devices are however a pain to extract from your usb-c slot. Well they do stick firmly in my new iMacs. But, they are most robust in use as the larger keys can be damaged by pressing the key each time you need to get access. This is mostly something to keep in mind when you’re using them on a notebook or such where the key is placed downwards. You only need to touch the metal conductor to activate the programmed code.
What sets the YubiKey 5 Series apart from the competition isn’t just the variety of form factors, as each one can function as a Smart Card (PIV), which can generate one-time passwords, support both OATH-TOTP and OATH-HOTP, and can be used for challenge-response authentication. All four devices support three cryptographic algorithms: RSA 4096, ECC p256, and ECC p384. These devices offer many different roles, often at the same time—provided you know what you’re doing as you need to understand what you’re doing when using the makers YubiKey Personalization Tool and/or Yubikey Manager software. These software programs offer a world of security settings which you need to be familiar with before just enter a setting.
Which YubiKey device you purchase will largely depend on what context you plan on using it. The Nano devices are useful if you plan on using them with a trusted computer, and you know you’ll need to access the YubiKey often. The full-size keys are better for hanging on a keyring and keeping close at hand for use.
**I will mention right now before describing how to use and experience its value, that you NEED TO have 2 YubiKey’s in your possession. You absolutely need a ‘Backup Yubikey’ in case you loose one or fails. If you don’t have a backup you will be faced with a real problem entering the site/host/mailbox you’ve secured !!
WORKING WITH YUBIKEY 5 NFC
To help you get started, Yubico has created a handy guide for new users. Just pick the YubiKey device you have, and the site displays a list of all the places and contexts you can use your YubiKey. Some of these link directly to a site or service’s onboarding page, while others provide instructions you have to follow yourself. The guide discussed on Yubikey’s website ( https://www.yubico.com/works-with-yubikey/catalog/ ) shows you all services working with YubiKey. All mentioned services provide a ‘How To’ to set the wanted 2FA with your KubiKey, mostly you need to go to the security page in order to set your key. As mentioned earlier you need to have a backup key in case of loss, key fail or whatever issue that makes you need your YubiKey, so if you set one key, do the same again and use the second key for the same account. This backup key needs to be stored in a safe place of course.
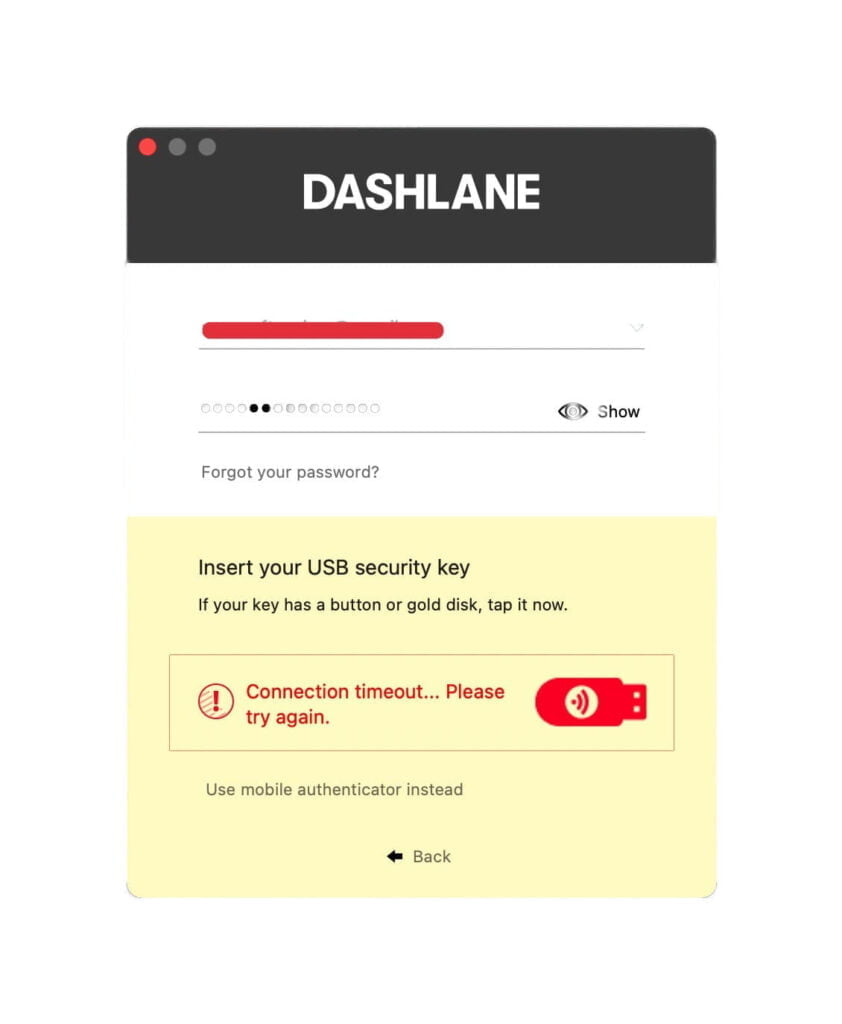
When you setup the Yubikey as a U2F security key like in the image below to activate the sign in, just touch or tap the ‘metal’ ( copper insert ) of the key and like magic you’re authorised. I just can’t express it enough times that having this kind of security is a vital step in security of your data. You can also use the key for entering your Mac or PC which makes it an extra safety feature next to the ‘FileVault’ encryption of your Mac SSD or Fusion Drive.
The YubiKey 5 Series can authenticate you in a number of ways, not just via U2F. With LastPass or Dashlane, for instance, you enroll the YubiKey to generate one-time passwords (specifically HMAC-based One-time Passwords, but I’ll use OTP for brevity) with a tap. This is different from U2F but it in practice it feels very similar. Log in to LastPass, navigate to the appropriate part of the Settings menu, click on the text field, and tap the YubiKey. A string of letters spews out, and that’s it! Now when you want to log in to LastPass, you’ll be prompted to plug in your YubiKey to have it spit out more OTPs.
Google Authenticator is an well known app you probably are familiar with, which generates six-digit passcodes every 30 seconds. This technology, more generally, is called Time-based One-time Passwords (TOTPs) and it’s one of the most common forms for 2FA used today along with DUO app.
Plug in your YubiKey 5, and launch the Yubico Authenticator application (https://www.yubico.com/products/services-software/download/yubico-authenticator/#download_here ), now navigate to a site that supports Google Authenticator for iPhone or a similar service. To secure a Google Account, for example, click the option to enroll a new phone with the authenticator app. When clicked a QR code usually appears at this point, and a prompt pops-up to scan with the appropriate authenticator app. Another method is to select a menu option in the Yubico Authenticator Desktop app and capture the QR code from your screen. A few more next-clicks, and the app starts providing unique six-digit codes every 30 seconds.
The security level is that the Yubico app (desktop ) cannot generate TOTPs without the presence of your YubiKey 5. The Yubico Authenticator stores data directly on your YubiKey and not on your computer. Pull the Yubikey out, and the Authenticator app can’t make new TOTPs. This basic procedure could add security problems, if someone steals or gets access to your YubiKey used to generate your TOTPs. So you best lock your YubiKey with a password with the Yubico Authenticator App, to even if it were stolen can’t be used for generating TOTPs.
YubiKey 5 Series is able to do much more:
– use it as a smartcard to log in to my desktop computer.
– use it log in to SSH servers.
– generate a PGP key and then use the YubiKey to sign or authenticate.
PRO
- Durable, construction.
- No batteries or moving parts.
- NFC capable.
- Different form-factors.
- Supports FIDO U2F, FIDO2.
- Can generate six-digit one-time use passcodes with Yubico Autenticator app.
- Supports multiple protocols for different security roles.
CONS
- Not cheap, but security comes at a price.
- Requires real effort and learning to fully realise its potential.
- Limited iOS integration.
VERDICT
The YubiKey 5 Series is are top notch devices providing the best security and a huge number of options. Choosing the key you need is not too difficult when you follow the website’s quiz. We use it, and will keep using it, however using the Yubikey takes a real learning curve. Just using it for Gmail protection and access to your Mac shouldn’t be e real problem. But YubiKey can so so much more and take security to a new level, a level such good that big commercial companies use it to stop or minimise data breach. Its well build, where the nano versions can be difficult to remove on usb-c slots. To make security really work you need to have a backup key as well, just in case you loose the (pin-locked) Yubikey. This is essential as you’re stuck without a backup. To me I feel so much more assured of my data not floating around for grabs, as all email-addresses are using YubiKey 5 NFC as do some websites providing the use of a 2FA tool like Yubikey. Is it cheap ? No, but how will you feel when your data is breached, hacked by criminals! Its worth every penny to better be safe than sorry.

0 Comments